How to Give User Only Read Access Domain Users
By default, simply members of the Domain Admins group have the remote RDP access to the Active Directory domain controllers' desktop. In this article nosotros'll prove how to grant RDP access to domain controllers for not-admin user accounts without granting administrative privileges.
Many of you can quite reasonably ask: why would ordinary domain users should have access to the DC desktop? Indeed, in modest or middle size infrastructures, when several administrators with the privileges of domain admins maintain them, you'll hardly need this. In most cases, delegating some authoritative permissions in Active Directory or using PowerShell Just Plenty Administration (JEA) is sufficient.
Still, in large corporate networks maintained by many administrators, it may become necessary to grant RDP access to the DC (usually to co-operative office DC's or RODC) for different server admin groups, monitoring team, on-duty administrators, or other technical staffs. As well, from time to fourth dimension some of the third-party services, not managed by the domain administrators, are deployed on the DC, and there's a need to maintain these services.
Contents:
- To Sign in Remotely, Y'all Demand the Rights to Sign in through Remote Desktop Services
- Group Policy: Allow Log on through Remote Desktop Services
- The Requested RDP Session Access is Denied
Tip. Microsoft doesn't recommend to install the Active Directory Domain Services and Remote Desktop Service role (terminal server) on a unmarried server. If in that location is simply one concrete server, on which you want to deploy both DC and RDS, you'd better utilize virtualization, since Microsoft virtualization licensing policy allows you to run two virtual servers under the same Windows Server Standard license.
To Sign in Remotely, Yous Need the Rights to Sign in through Remote Desktop Services
Subsequently the server has been promoted to the domain controller, you lot cannot manage local users and groups from the Computer Direction mmc snap-in. When y'all endeavour to open Local Users and Groups (lusrmgr.msc) console, the following error appears:
The estimator xxx is a domain controller. This snip-in cannot be used on a domain controller. Domain accounts are managed with the Active Directory Users and Computers snap-in.
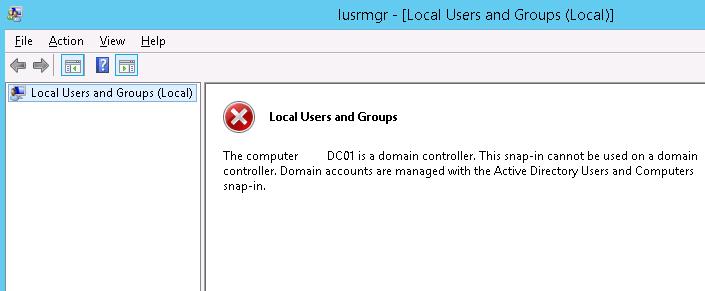
As yous can see, there are no local groups on the domain controller. Instead of the local group Remote Desktop Users, the DC uses the congenital-in domain group Remote Desktop Users (located in the Builtin container). You can manage this group from the ADUC console or from the command prompt on the DC.
Display the members of the domain group Remote Desktop Users on the domain controller using the command:
net localgroup "Remote Desktop Users"
As yous tin run into, it is empty. Add a domain user it-pro to it (in our example, it-pro is a regular domain user without authoritative privileges):
internet localgroup "Remote Desktop Users" /add corp\it-pro
Make sure that the user is added to this group:
net localgroup "Remote Desktop Users"

You tin can also verify that the user is now a member of the Remote Desktop Users domain group using the ADUC (dsa.msc) snap-in.
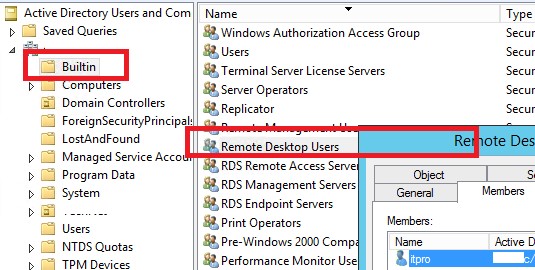
To sign in remotely, you demand the right to sign in through Remote Desktop Services. By default members of the Administrators grouping accept this right. If the group you're in does not have the right, or if the right has been removed from the Administrators grouping, you lot demand to be granted the correct manually.

Group Policy: Allow Log on through Remote Desktop Services
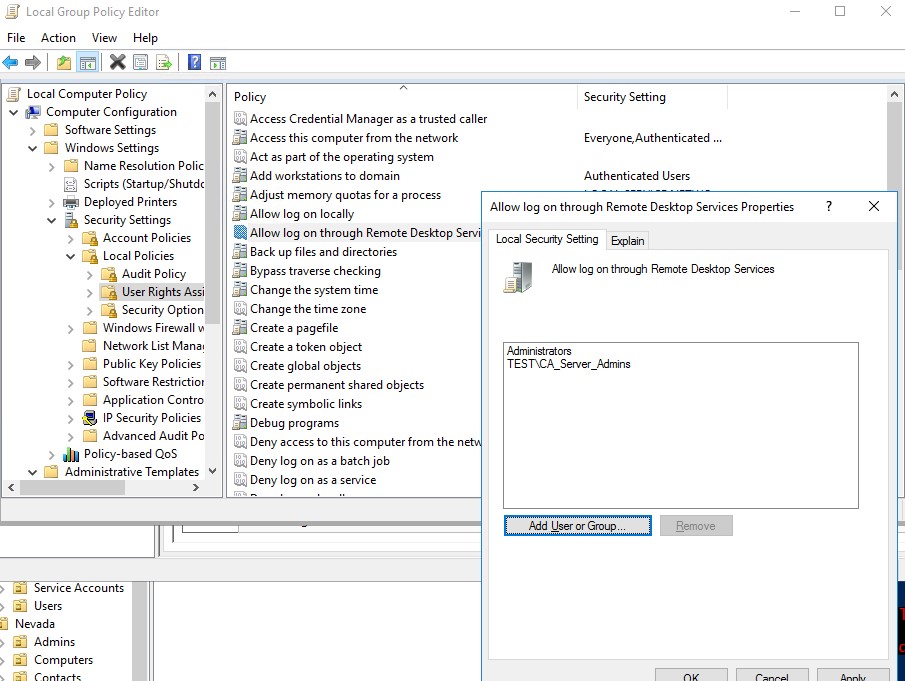
To let a domain user or grouping a remote RDP connection to Windows, you must grant information technology the SeRemoteInteractiveLogonRight privileges. By default, just members of the Administrators grouping have this right. You can grant this permission using the Let log on through Remote Desktop Services policy.
In Windows 2003 and older this policy is called Permit log on through terminal services.
To allow remote connection to the domain controllers for members of the Remote Desktop Users grouping you need to change the settings of this policy on your domain controller:
- Launch the Local Group Policy Editor (
gpedit.msc); - Go to the GPO section Reckoner Configuration -> Windows settings -> Security Settings -> Local policies -> User Rights Assignment;
- Find the policy Let log on through Remote Desktop Services;
Later the server is promoted to the DC, only the Administrators grouping (these are Domain Admins) remains in this local policy.
- Edit the policy, add the domain grouping Remote Desktop Users (like this:
domainname\Remote Desktop Users), or straight the domain user, or a group (domain\CA_Server_Admins) to information technology; - Update the Local Group Policy settings on the DC using the control:
gpupdate /force
Note that the group that yous added to the Allow log on through Remote Desktop Services policy should not be present in the "Deny log on through Remote Desktop Services" policy , considering it has a higher priority (check the commodity Restricting Network Access nether local accounts). In addition, if you lot are restricting the listing of computers on which users can log on, yous need to add the DC name to the properties of the Advertising account (LogonWorkstations user attribute).
Note. To let a user to log on to the DC locally (via the server panel), y'all must add the account or group to the policy "Allow log on locally". By default, this permission is allowed for the post-obit domain groups:
- Backup Operators
- Administrators
- Impress Operators
- Server Operators
- Business relationship Operators
Information technology is improve to create a new security group in the domain, for example, AllowLogonDC and add user accounts to it that need remote access to the DC. If yous want to allow access to all Advertising domain controllers at in one case, instead of editing of the Local Policy on each DC, information technology's better to add a the user group to the Default Domain Controllers Policy using the GPMC.msc console (change the policy settings in the same section: Computer Configuration\Windows Settings\Security Settings\Local Policies\User Rights Consignment -> Allow log on through Remote Desktop Services).
Alarm. If yous modify the Default Domain Controllers Policy, don't forget to add together the domain/enterprise administrator groups to the policy Allow log on through Remote Desktop Services, otherwise they volition lose remote access to the DCs.
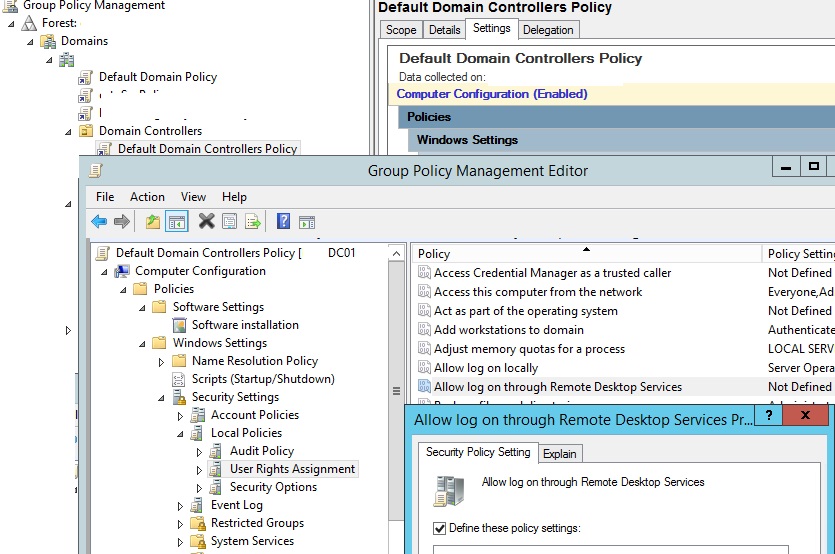
Now the users (groups) you added to the policy will be able to connect to the Advertizement domain controllers via RDP.
If you need to grant non-administrator users the permissions to start/finish sure services on a DC, use the post-obit guide.
The Requested RDP Session Access is Denied
In some cases, when connecting via RDP to a domain controller, an error may announced:
The requested session access is denied.
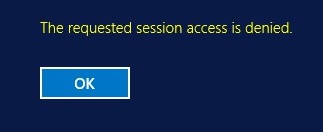
If yous are connecting to the DC under a non-admin user business relationship, this could be due to two bug:
- You are trying to connect to the server console (using the
mstsc /adminmode). This connectedness mode is but immune for administrators. Try to connect to the server using mstsc.exe client in normal RDP mode (without/adminchoice); - The server may already take 2 agile RDP sessions (past default, you can't use more ii simultaneously RDP sessions on Windows Server without RDS part). You cannot log off other users without ambassador permissions. You need to look for the administrators to release ane of the sessions.
Source: http://woshub.com/allow-non-administrators-rdp-access-to-domain-controller/
0 Response to "How to Give User Only Read Access Domain Users"
Post a Comment